Table of contents
Open Table of contents
- Introduction
- Case 1: PHP::strcmp() and Comparison Vulnerability
- Case 2: PHP::call_user_func to Execute Arbitrary Code
- Case 3: PHP::md5() and Comparison Vulnerability
- Case 4: PHP::include() and Local File Inclusion
- Case 5: SQL Injection
- Case 6: PHP::srand() & PHP::rand() and Predictable Random Number Generation
- Conclusion
Introduction
Capture The Flag (CTF) competitions have become a popular way for cybersecurity enthusiasts and professionals to test and enhance their skills. CTFs often simulate real-world scenarios where participants are required to solve various challenges in order to “capture the flag,” which serves as proof of success. In this post, I will explain some of the most common programming vulnerabilities that are used in CTF challenges. These vulnerabilities are often found in web applications and can be exploited by attackers to gain unauthorized access to the system.
Case 1: PHP::strcmp() and Comparison Vulnerability
<?php
define('FLAG', 'flag{this_is_a_fake_flag}');
if (strcmp(FLAG, $_GET['flag']) == 0) {
echo FLAG;
}
In this challenge, the goal is to retrieve the flag by exploiting the strcmp() function in PHP. The strcmp() function is used to compare two strings and returns 0 if they are equal. However, the vulnerability in this code lies in the fact that the strcmp() function is used with the == operator, which can be exploited by passing an array as the second argument to the function. By passing an array as the second argument, the strcmp() function will return NULL, which is not equal to 0, but the flag will be displayed.
To exploit this vulnerability, the following URL can be used:
http://target/?flag[]=1
By passing an array as the second argument to the strcmp() function, the flag will be displayed. In the latest versions of PHP, this vulnerability has been patched, but it is still commonly used in CTF challenges.
Case 2: PHP::call_user_func to Execute Arbitrary Code
<?php
call_user_func($_GET['func'], $_GET['param']);
In this challenge, the goal is to execute arbitrary PHP code by exploiting the call_user_func() function. The call_user_func() function is used to call a user-defined function, and it can be exploited by passing a function name as a parameter in the URL. By passing a function name as a parameter, the function will be executed, and the flag will be displayed.
To exploit this vulnerability, the following URL can be used:
http://target/?func=system¶m=cat+/flag.txt
By passing the system function as a parameter, the cat /etc/passwd command will be executed, and the flag will be displayed. This vulnerability can be used to execute arbitrary code on the server and is commonly found in CTF challenges.
Case 3: PHP::md5() and Comparison Vulnerability
<?php
define('FLAG', 'flag{this_is_a_fake_flag}');
if (md5($_GET['flag']) == '0e462097431906509019562988736854') {
echo FLAG;
}
In this challenge, the goal is to retrieve the flag by exploiting the md5() function in PHP. The vulnerability in this code lies in the fact that the md5() function is used with the == operator, which can be exploited by passing a string that its hash starts with 0e.
To exploit this vulnerability, the following URL can be used:
http://target/?flag=QNKCDZO
By passing the string QNKCDZO as the parameter, the md5() function will return a hash that starts with 0e, and the flag will be displayed.
Case 4: PHP::include() and Local File Inclusion
<?php
define('FLAG', 'flag{this_is_a_fake_flag}');
include $_GET['file'];
Explanation: php://filter is a stream filter that allows you to read data from a file and apply filters to it. By using the php://filter stream filter, you can read the contents of a file and apply filters to it. In this challenge, the goal is to retrieve the flag by exploiting the php://filter stream filter. The vulnerability in this code lies in the fact that the include function is used with the $_GET parameter, which can be exploited by passing a URL that starts with php://filter.
To exploit this vulnerability, the following URL can be used:
http://target/?file=php://filter/convert.base64-encode/resource=index.php
By passing the php://filter stream filter as the parameter, the contents of the index.php file will be encoded in base64, and the flag will be displayed. This vulnerability can be used to read the contents of files on the server.
Case 5: SQL Injection
<?php
$keywords = $this-request->get('keywords');
$where = "title LIKE '%$keywords%'";
return json(Db::name('articles')->where($where)->select());
In this challenge, the goal is to retrieve the flag by exploiting a SQL injection vulnerability. The vulnerability in this code lies in the fact that the user input is directly concatenated into the SQL query without any sanitization or validation. This allows an attacker to inject SQL code into the query and retrieve sensitive information from the database.
To exploit this vulnerability, I make the following sql command:
SELECT * FROM `articles` WHERE ( title LIKE '%1' ) UNION SELECT * FROM `admin` WHERE ( 1 AND '%'='%')
By passing the following URL as the parameter:
http://target/?keywords=1%27%29UNION%20SELECT%20*%20FROM%20%60admin%60%20WHERE%20%281%20AND%20%27%27%3D%27
Then I got the result:
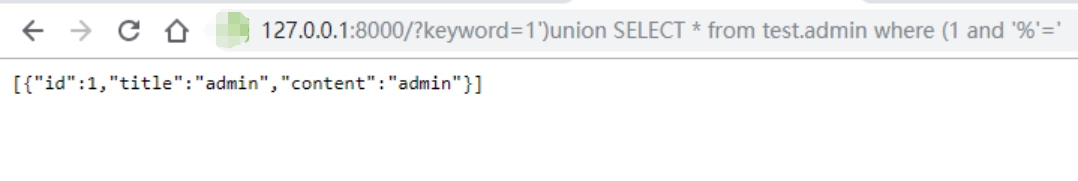
By injecting the SQL code into the query, the flag will be displayed. This vulnerability can be used to retrieve sensitive information from the database and is commonly found in web applications.
Case 6: PHP::srand() & PHP::rand() and Predictable Random Number Generation
function encrypt($str)
{
$cryptedstr = "";
srand(3284724);
for ($i = 0; $i < strlen($str); $i++)
{
$temp = ord(substr($str, $i, 1)) ^ rand(0, 255);
while(strlen($temp)<3)
{
$temp = "0".$temp;
}
$cryptedstr .= $temp. "";
}
return base64_encode($cryptedstr);
}
function decrypt($str)
{
$str = base64_decode($str);
$destr = '';
srand(3284724);
for ($i = 0; $i < strlen($str); $i += 3)
{
$temp = intval(substr($str, $i, 3));
$temp = $temp ^ rand(0, 255);
$destr .= chr($temp);
}
return $destr;
}
In this challenge, the goal is to decrypt the encrypted string by exploiting the predictable random number generation in PHP. The vulnerability in this code lies in the fact that the srand() and rand() functions are used to generate random numbers, but the seed value is fixed, which makes the random number generation predictable. By knowing the seed value, an attacker can predict the random numbers generated by the rand() function and decrypt the encrypted string.
Conclusion
In this post, I have explained some of the most common programming vulnerabilities that are used in CTF challenges. These vulnerabilities can be exploited by attackers to gain unauthorized access to the system and are often found in web applications. By understanding these vulnerabilities and how they can be exploited, participants in CTF competitions can enhance their skills and learn how to secure their own applications against such attacks.